Why Open Source Security Matters?: A Guide to Managing Security Risks in Open Source Software
Many businesses now run on open-source software for mission-critical functions, a trend that has only accelerated in recent years. Although there are many advantages to using open sources, such as reduced costs and greater adaptability, there are also security dangers that must be mitigated. In this article, we'll discuss the significance of open-source security and offer advice for dealing with potential threats in open-source programs.
Why Open Source Security Matters?

Open-source software is developed collaboratively by a community of developers who contribute code and make it freely available for anyone to use. While this collaborative approach can lead to innovation and rapid development, it also presents unique security challenges. Here are some reasons why open-source security matters:
Vulnerabilities can go unnoticed: Since open source is developed by a community of volunteers, there may not be a dedicated team responsible for identifying and fixing vulnerabilities. This means that vulnerabilities can go unnoticed for longer periods of time.
Attackers can easily access the code: Since open-source code is freely available, attackers can easily access it and identify vulnerabilities that they can exploit.
Dependencies can introduce additional risks: Open-source software often relies on other open-source libraries or frameworks, which introduces additional risks if those dependencies have vulnerabilities.
Managing Security Risks in Open Source Software

To manage security risks in open-source software, here are some best practices you should follow:
Keep your dependencies up-to-date: Regularly update your dependencies to ensure that you're using the latest version with any known vulnerabilities patched.
Monitor for vulnerabilities: Use tools like vulnerability scanners or threat intelligence feeds to monitor for known vulnerabilities in your open-source components.
Conduct regular code reviews: Review the code of your open-source components regularly to identify any potential issues or vulnerabilities.
Use trusted sources: Only use trusted sources when downloading or updating your open-source components to reduce the risk of downloading malicious code.
Have a plan in place: Have a plan in place to respond to security incidents and vulnerabilities in your open-source software.
The Importance of Open Source Security for Businesses
While open-source software has many benefits, it also comes with its own set of security dangers that companies must learn to mitigate. The financial and reputational repercussions of a security breach in open-source software can be substantial for enterprises. A security breach, for instance, might cause financial losses, hurt the company's reputation, and land it in legal hot water. Businesses should take preventative measures regarding open-source security in order to lessen the impact of these threats. This involves doing things like keeping dependencies up to current, checking for vulnerabilities and having a plan in place for handling security problems.
Case Studies
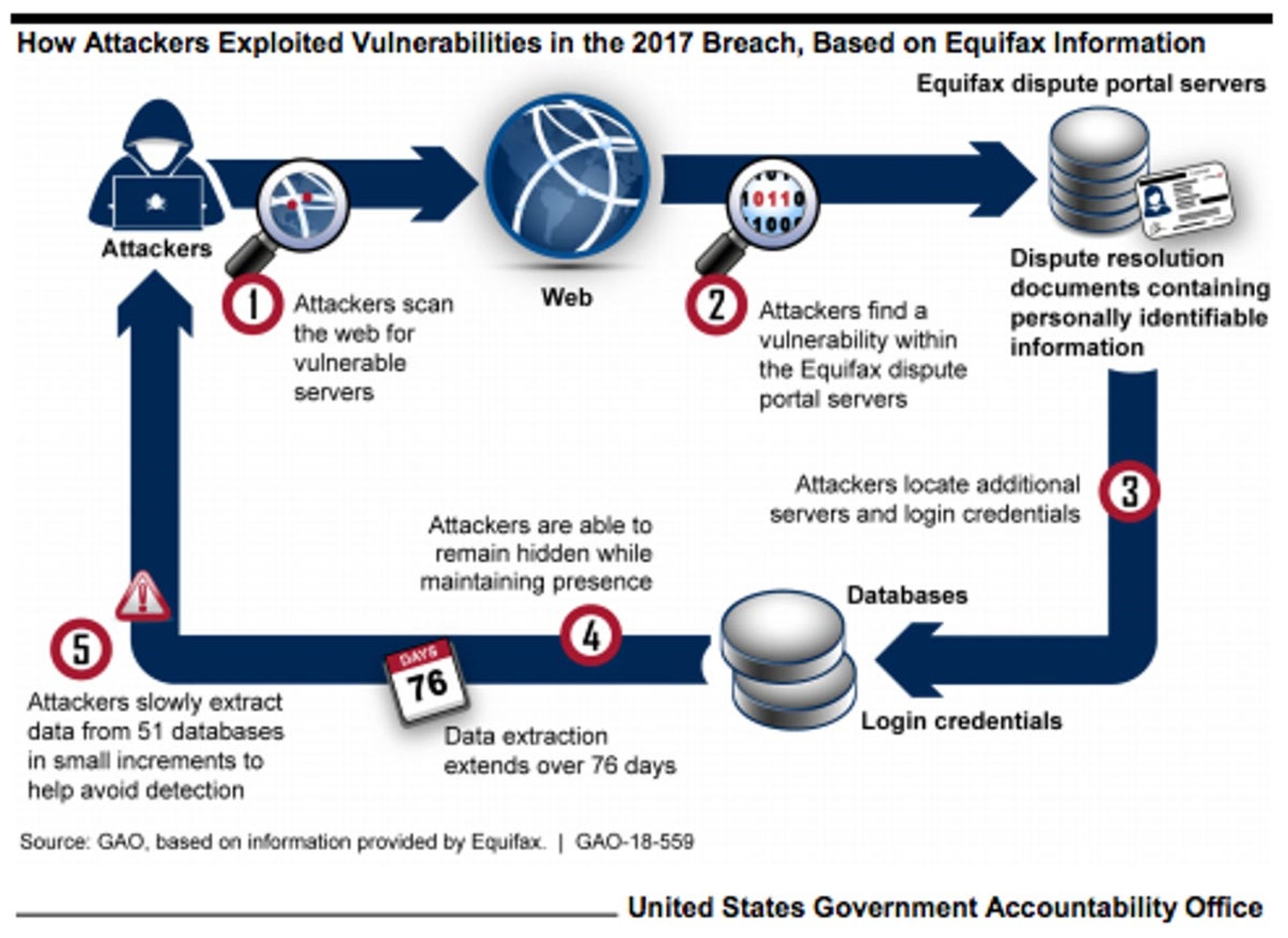
Here are a few examples of real-world incidents related to open-source security:
The Heartbleed Bug: In 2014, a vulnerability known as the Heartbleed bug was discovered in OpenSSL, an open-source cryptography library. The bug allowed attackers to access sensitive information like passwords and encryption keys from vulnerable systems. The incident highlighted the need for better management of security risks in open-source software.
Equifax Data Breach: In 2017, Equifax suffered a massive data breach that exposed the personal information of millions of people. The breach was caused by a vulnerability in Apache Struts, an open-source web application framework. The incident demonstrated the potential financial and reputational costs of a security breach in open-source software.
How Onboardbase Can Help?

We at Onboardbase are aware of the significance of open-source safety measures. Because of this, we offer a safe environment in which you may store and manage your open-source parts. To help you locate and control any security flaws in your open-source software, our platform provides tools like automatic vulnerability scanning, dependency management, and code reviews. Your open-source components may be trusted to be up-to-date and safe with Onboardbase.
Conclusion
While there are numerous advantages to using open-source software, there are also some security dangers that must be addressed. The likelihood of security issues in your open-source software can be mitigated by adhering to best practices such maintaining up-to-date dependencies, checking for vulnerabilities, performing regular code reviews, relying on reliable sources, and having a plan in place. You can rest assured that you are meeting your open-source security obligations with the help of Onboardbase's protected platform for managing open-source components.

